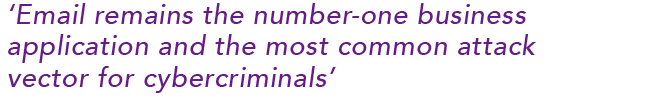Among all the modern high-tech buzzwords, there’s one that the people of Johannesburg don’t need to have explained. In mid-2019, one of the South African city’s major electricity suppliers was hit by a ransomware attack that locked more than a quarter of a million residents out of their pre-paid electricity accounts. City Power confirmed that a virus had shut down its IT systems, tweeting: ‘It has encrypted all our databases, applications and network.’ Barely a month later, a leaked UN Security Council report included South Africa in a list of countries whose cryptocurrency exchanges had been targeted by North Korean hackers in a US$2 billion attack.
Africa – its governments, businesses, organisations and private computer users – has long been at high risk of cyberattack. Speaking to Michiel Jonker, director of IT advisory at accounting group BDO South Africa, it’s clear that the situation is not improving. ‘It’s getting worse,’ he says. ‘Many security incidents occur due to the lack of updated software. In other words, organisations are not always doing their patching as they should. Over and above the lack of patching, we also find that the lack of financial resources in Africa makes it difficult for huge organisations to upgrade to newer versions of software. As a result, they still run legacy software that is no longer supported by the software vendor, opening themselves up to an increasing risk of security incidents.’
Lukas van der Merwe, specialist sales executive of security at T-Systems South Africa, points to that City Power attack as proof of how easy it is for African organisations to fall victim to cybercriminals. ‘While [City Power] did not reveal how much the attackers demanded for decrypting its systems, one can imagine that it was most likely a significant amount,’ he says. ‘In cases like this, there is no guarantee that once the ransom is paid the data will be decrypted or that the perpetrators will not attack again. It is strongly advised against paying the ransom.’
But if cure – or payment – isn’t an option, then all that’s left is prevention… Or sitting back and waiting for the inevitable to happen.
Jonker prefers prevention – or what BDO calls ‘cyberdefence’. He explains that cyber-security is a broad term that also covers cyberdefence. ‘Cyberdefence is primarily concerned about the prevention of cybercrime/incidents. Cybersecurity entails a lot more than just the prevention of cyber incidents. For example, it is guaranteed that preventive controls will fail at some point in time and, when they do, other types of controls have to come into operation – for example, detective and corrective controls. In the future we will have to rely more on detective and corrective controls, as preventive controls are bound to fail spectacularly.’
He points to research that suggests the average time hackers spend on an internal network, without detection, is 200 days. ‘This statistic indicates that preventive controls can fail but it also goes to show that, currently, organisations do not have proper detective controls in place to detect a breach and to correct it as soon as possible,’ he says. ‘Thus, organisations still have a narrow focus of cybersecurity – in other words, by primarily focusing on prevention [defence], instead of embracing a holistic view. This holistic view should also include other aspects of cyber-security, namely data privacy, disaster recovery, cyber risk and strategy, and cyber insurance.’
Still, many organisations seem resigned to await attack. The 2019 global State of Email Security Report, released by Mimecast, found that fewer than half of South African respondents have a cyber-resilience strategy in place, even though 44% believed they would suffer negative business impact from an email-borne attack. Nearly 10% of businesses said a cyber-attack was indeed inevitable.
‘Organisations should strive for stronger cyber-resilience,’ says Mimecast cybersecurity expert Paul Stafford. ‘This means putting comprehensive security controls in place to detect and prevent cyberthreats; powerful business continuity tools to maintain productivity during an attack; automated backup and recovery capabilities that quickly restore critical data and systems after an attack; and a focus on empowering employees with ongoing cybersecurity awareness training.’
Stafford says that it all starts with email. ‘Email remains the number-one business application and the most common attack vector for cybercriminals.’ He warns that nine in 10 cyberattacks use email as its primary channel of attack. ‘And yet, organisations still don’t have the right measures in place to ensure this channel of communication is adequately protected,’ he says.
But email is just one platform, and only one unlocked entrance through which cyber-criminals can sneak in. Consider how many companies across Africa are using mobile apps – from WhatsApp to Slack to Google Hangouts, Discord, Microsoft Teams and more – to manage their internal communications.

‘Apps pose a real problem for mobile users who give them sweeping permissions but don’t always check security,’ says Riaan Badenhorst, GM for Kaspersky in Africa. These are typically free apps found in official app stores that perform as advertised, but also send personal – and potentially, corporate – data to a remote server, where it is mined by advertisers or even cybercriminals. Data leakage can also happen through hostile enterprise-signed mobile apps. Here, mobile malware uses distribution code native to popular mobile operating systems like iOS and Android to spread valuable data across corporate networks without raising red flags.’
Like email, the mobile app problem is only going to get worse. As Badenhorst points out, the number of worldwide mobile-phone users was forecast to reach 4.68 billion in 2019, of whom 2.7 billion are smartphone users. Android users can currently choose between 2.46 million apps (Apple users aren’t far behind on 1.96 million), with the average smartphone user estimated to have between 60 and 90 apps installed on their phone. Add in factors such as unsecured WiFi connections, network spoofing, phishing attacks, ransomware, spyware and improper session handling, and – as Badenhorst puts it – ‘mobile devices make for the perfect easy target’.
While email and mobile apps may be a cybersecurity blind spot for many organisations, there’s a growing awareness – or at least a wariness – of the security threats related to enterprise cloud migration.
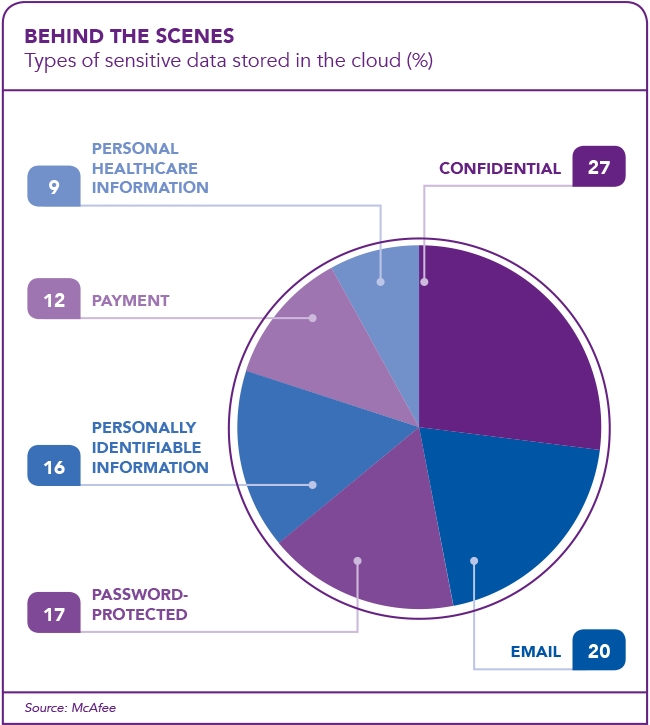
In its 2019 Cloud Adoption and Risk Report, security company McAfee found that 21% of all files in the cloud contain sensitive data. ‘So not only do most organisations place trust in their public cloud service providers to store their sensitive data; nearly a quarter of all data in the cloud meets the need for stringent protection,’ the report notes.The problem here is not that the information is being saved in the cloud; the problem is the widespread – and wrong – assumption that just because data is saved on the cloud, it is done so securely with no danger of being compromised.
‘There is a perception among many African business executives that when IT applications were migrated to the cloud, that accountability for security had also been transferred to the cloud service provider,’ says Jonker. ‘Further, based on promises made by cloud service providers, business executives believe that their applications are more secure than having them hosted on [the premises]. The fact of the matter is that an organisation who migrated to the cloud is still accountable for proper cybersecurity. They even have certain responsibilities that cannot be transferred to the cloud service provider. And applications in the cloud are just as vulnerable to cyberthreats as applications in your own server room.’
Jonker says that during the course of its work, BDO has found that in Africa many organisations use cloud services without proper service level agreements (SLAs) in place. ‘An SLA is the only mechanism an organisation has to demand proper security controls from a cloud service provider,’ he says.
Still, going through the fine print of your SLA won’t help you much when your organisation’s confidential information has been leaked, or when it’s being held to ransom by cybercriminals who’ve penetrated the defences of your email, apps or cloud platform.
Just ask the powerless people in Johannesburg whose pre-paid electricity accounts were hacked.