The password is dead. In the post-privacy, post-GDPR world of modern data security, your old p@ssword123 just doesn’t cut it any more. Today, it’s all about biometrics.
Biometric identification – which uses fingerprints, faces and other physical features – allows end users to provide unique physiological characteristics instead of passwords or personal identification numbers (PINs), in effect replacing ‘something you have’ with ‘who you are’. The former is discoverable and hackable; the second is unique to you.
At least, that’s the theory. In Deloitte’s seventh annual Mobile Consumer Survey, the firm estimates that 15 million consumers in the UK now have a smartphone that incorporates a fingerprint scanner. That’s about 36% of the user base, with 79% of them actually using the technology. The most common biometric application, at 96%, is to unlock the phone. ‘Most smartphone owners use biometric authentication because it is faster and more secure than traditional methods,’ says Paul Lee, Deloitte’s head of research for technology, media and telecoms.
‘Passwords have to be ever longer and more complex in order to be secure, which makes them hard to remember. For the modern-day smartphone user, a quick scan of a thumb is faster and just as secure, if not more so – and fingerprints are not forgettable. We estimate that currently, globally, well over a billion devices now include a fingerprint reader.’
Deloitte’s report found that new 3D facial scanners can be even more secure than fingerprint readers. To put this in a smartphone context, the technology is moving beyond using your thumb to activate your iPhone’s home button, and deeper into the facial recognition software that drives social apps such as Snapchat or Facebook’s photo-tagging service. ‘By the end of 2018, it is likely that 3D facial recognition will be used more frequently than fingerprint scanners in smartphones,’ says Lee. ‘We expect that individual usage of 3D facial recognition sensors will be over 100 times daily on average.’
Yet the application goes beyond smartphone access and into the broader fields of identification and access control. In 2018, for example, smart technology firm Jasco installed the Touchless Biometric (TBS) Access Control System – from its security portfolio – at its head office in Gauteng, South Africa. The system was deployed in less than two months (including enrolling all employees and their biometrics on a centralised database) and the firm holds it as ‘a working, live demonstration of the solution for customers’.
The company says the system allows for easy movement within the building, and is more hygienic than previous solutions as the touchless 3D technology requires little to no physical contact. ‘The solution also negates the need for carrying ID access cards or remembering PIN codes,’ according to Peter Stutz, Jasco portfolio manager: IT infrastructure.

‘The likes of access cards can go missing or be stolen, and PIN codes can be forgotten, which creates an unnecessary security risk. Stolen or lost cards can be used by unauthorised personnel to access restricted areas, and people often unwittingly help their colleagues gain access by letting them through with their own card or PIN, not knowing whether or not their colleague is permitted to be in that particular area.’
The notion of using technology to govern access control is, of course, nothing new. But the way in which identity is confirmed and access is authorised is changing. Government, too, is harnessing this maturing technology. In 2018, South Africa’s Department of Home Affairs launched its new automated biometric identification system, which promises to offer a single view of citizens across the life cycle and their status change at various stages. It replaces the Home Affairs National Identity System, which the department described as being manually operated and outdated.
The South African Post Office has also deployed a biometrics firm to ensure officials distribute South Africa Social Security Agency (SASSA) grant payments to the correct recipients. The system allows officials to biometrically verify SASSA card recipients, with a view to reducing fraud. Meanwhile, First National Bank (FNB) recently launched TouchPoint, a mini-ATM that grants customers login access to their accounts via fingerprint. The device acts as a self-service kiosk, enabling users to make withdrawals, transfers and payments, view statements, buy airtime and electricity, and perform card cancellations.
‘The TouchPoint validates a customer’s identity by scanning a fingerprint placed on the biometric reader, and it can detect false fingerprints to prevent fraud. The identity of the customer is then verified with the Department of Home Affairs to ensure the self-service account opening complies with the relevant laws,’ says Lee-Anne van Zyl, CEO of FNB Points of Presence. ‘The introduction of biometric validation on self-service devices is an important step to making banking much more accessible to South African communities. As the use of biometric technology becomes more pervasive in the everyday life of customers, it’s important to use this technology to accelerate access to banking services.’
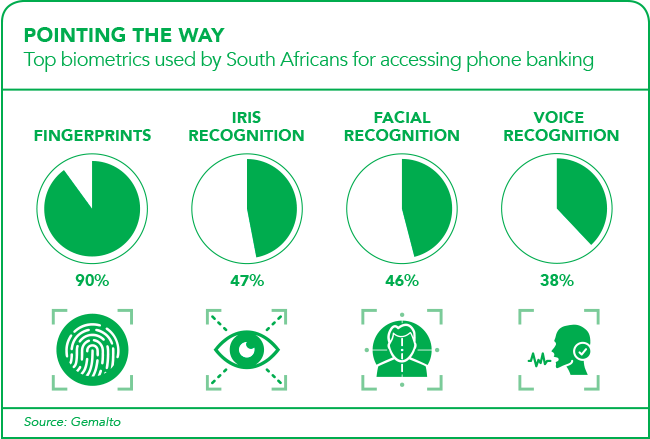
However, as biometric technology becomes more prevalent, there’s an even greater need for the systems to work as they should. In its latest e-banking survey, global digital security firm Gemalto found that 87% of South African respondents were willing to use biometrics because they believed it to be more secure.The trouble is, biometrics has an Achilles heel, in that you only have one face and one set of fingerprints. And while you can reset your password if it’s compromised, you can’t reset your head or hands if hackers get access to the database where your biometric information is stored. That’s exactly what happened to the United States Office of Personnel Management in 2015, when hackers accessed the fingerprints of 5.6 million US federal employees. At the time, the New York Times reported that the hack was believed to be the work of Chinese intelligence agents, prompting one senior intelligence source to shrug: ‘I am assuming there will be people we simply can’t send to China.’

As Marius Coetzee, CEO of South African identity management firm Ideco, writes in a blog, inadequate biometrics systems could be creating a false sense of security among enterprises. ‘This is because not all fingerprint readers are created equal,’ he writes. ‘Although all fingerprint readers use minutiae points to match fingerprints, not all have the ability to detect the difference between real minutiae of a fingerprint and spoofed minutiae.’
Coetzee adds that a simple trick can allow criminals to hack a fingerprint reader. ‘The simplest methods are simply to wind thin thread around the fingertip, or to introduce a series of cuts to the fingerprint. This creates scores of new minutiae points, increasing the risk that the spoofed fingerprint will be a close enough match to that of an authorised person on the estate or bank database.’
Researchers at the State University of New York at Buffalo may have a solution. In October, assistant professors Wenyao Xu and Feng Lin, together with associate professor Zhanpeng Jin, proposed what they call a brain password. ‘When a person looks at a photograph or hears a piece of music, their brain responds in ways that researchers or medical professionals can measure with electrical sensors placed on their scalp,’ they wrote for the Conversation. ‘We have discovered that every person’s brain responds differently to an external stimulus, so even if two people look at the same photograph, readings of their brain activity will be different. This process is automatic and unconscious, so a person can’t control what brain response happens. And every time [someone] sees a photo of a particular celebrity, their brain reacts the same way – though differently from everyone else’s.’
This, they realised, creates an opportunity for a unique combination that can serve as an advanced biometric access control system, you would use a special that or headset, that reads your brainwaves as you watch a sequence of images. ‘A computer system would compare their brain waves at that moment to what had been stored initially – and either grant access or deny it, depending on the results,’ the team writes. ‘It would take about five seconds, not much longer than entering a password or typing a PIN into a number keypad.’
Brainwave technology is still in its early stages, but it’s already light years ahead of your old ‘p@ssword123’ – let alone your fingerprints. What more, it’s hard to imagine criminals finding a way to access or compromise your brain. But then again, that’s exactly what they would want you to think.