You have already been hacked. Chances are, your IT security has been breached, and your systems and information compromised. And even if you haven’t been hacked, you should still act like you have. According to IT solutions firm Citrix South Africa country manager Brendan McAravey: ‘The fact that many organisations go months before they realise they have been compromised means there are not enough tools in place to quickly detect “indicators of attack” and “indicators of compromise”.’
McAravey adds that this is true ‘irrespective of customer or industry sector’. His advice? ‘You have to act like you’ve already been breached. That’s the change of mindset you need. Assume you are compromised right now, today, and then think about how you would architect segmentation at the access, network, application and data level,’ he says.
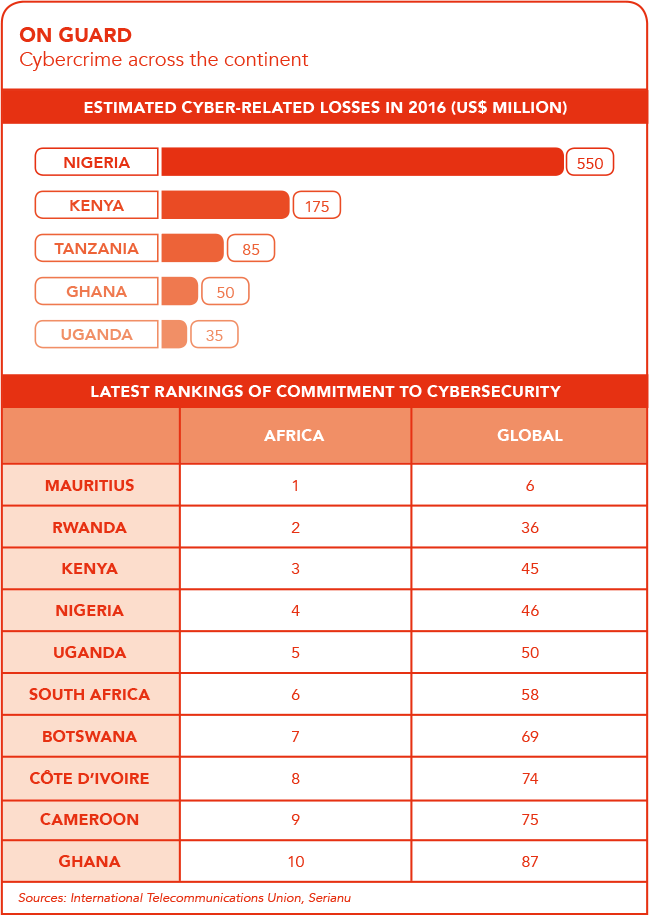
He references various reports to prove his point, such as the one by Allianz Global Corporate and Specialty, which found that cybercrime in South Africa costs the economy an estimated ZAR6 billion annually. Then there’s another from the International Telecommunication Union (ITU), which found that in 2016, one in every 131 emails sent worldwide was malicious – the highest rate in five years. The average malware-related ransom demand rose threefold in just a year to more than US$1 000, according to the ITU.
In a world like that, you have to assume the worst. You can’t afford not to. ‘Put simply, it is my view that it’s no longer possible to protect your personal data or your organisation’s intellectual property by maintaining a reactive strategy,’ says McAravey. ‘At the heart of many of the best examples of modern, effective security postures that I have seen has been the concept of using intelligence to help drive the desired outcomes of each of the key cornerstones of deter, detect, respond, remediate.
‘Just as in the physical world, we look to law enforcement and government entities to use intelligence to protect from harm, so must we embrace the same philosophies in the virtual world. We are in a relentless state of cyberwar and we must prepare for the ongoing battle by out-thinking and out-smarting the enemy,’ he says.
Using language such as ‘war’, ‘battle’ and ‘enemy’ sounds like an overstatement or overreaction … until you realise the full extent – the volume, variety and velocity – of the problem. ‘It is not uncommon for a large organisation to receive over 10 000 security alerts a day,’ says Patrick Rhude, head of product management at Nokia’s security product unit. The problem, he says, is that faulty intelligence data often produces duplicate information and false alerts. When combined with the limited capacity of security analysts, it means that only a small portion of those alerts are ever investigated.
‘It is therefore crucial that security analytics, machine learning and automation are incorporated into security management,’ says Rhude. ‘We have already seen a shift towards adopting multi-dimensional security analytics. This enables security organisations to correlate data from multiple domains and helps identify suspicious, malicious or inadvertent anomalies.’
According to Rhude, in-depth security analytics enable organisations to gather data about the threat – and when that information is combined with threat intelligence data, you can detect threats and prescribe the appropriate response more effectively, providing strategic mitigation to strategic threats.
That’s ‘mitigation’, though – not ‘eradication’ or ‘complete prevention’. Wimpie du Plessis, operations officer of security at Internet Solutions, is very clear about this. ‘It’s important for companies to acknowledge that there is no such thing as 100% protection against cyberattacks,’ he says. ‘This is why it is critical to plan both for attack and response.’
Du Plessis explains that basic, foundation controls must be in place, and must be implemented effectively and monitored on a continuous basis. ‘To illustrate using an analogy, kitting your house with the latest high-tech security system, including exterior beams, CCTV cameras and an electric fence is null and void if you leave the gate and front door open,’ he says.

Speaking at the recent StartUP Nigeria event held in Lagos, Isa Pantami, director general of Nigeria’s National Information Technology Development Agency, identified cybersecurity awareness as one of the agency’s key priorities. And no wonder. He cited a report that shows that Nigeria loses an amount of almost NGN78 billion every year through cybercrime. Pantami stated that awareness alone could help reduce Nigeria’s cyber-related losses by up to 70%.
The number sounds laughable, but it’s probably not too far off the mark. More often than not, it’s an organisation’s own employees who are leaving the proverbial front door open. Du Plessis points to the recent WannaCry malware attack – which infected in excess of 230 000 computers in more than 150 countries on day one alone – as a prime example.
Ian Russell, engagement manager at networking and infrastructure business Aptronics, agrees. ‘WannaCry, like so many similar attacks, all began with a simple-looking email,’ he says. ‘So small and innocent at first, but the email set into motion a chain of events that saw WannaCry grow to historic proportions in no time. Email, therefore, should be the first place an organisation looks when identifying digital security weaknesses. Unfortunately, email security is about more than settings and firewalls – even more critically, it’s about the people that use it.’
According to Russell, incidents such as these succeed because of a combination of outdated systems and lack of staff education. He adds that employees are increasingly susceptible to phishing attacks thanks to advanced social engineering. ‘Regular and supportive – rather than punitive – employee education is important to guard against these vulnerabilities,’ he says. ‘Campaigns should be run for all employees, from the boardroom to the basement, to ensure constant education, awareness and understanding for all in the company. The human component of security is very important when developing a strategy. Once these foundational elements are in place, companies can then move on to more higher level controls, such as big-data analytics.’
Speaking directly to the threat of ransomware, and to cybersecurity in general, Russell recommends following the 3-2-1 rule: making three copies of anything you care about, saving it in two different formats, and ensuring you always have one off-site backup. ‘Cyberattacks should not be addressed reactively, but anticipated and planned for at every organisational level,’ he says.
‘The best advice for digital safety, and the thing that all three of those tips have in common, is simple – play it safe. A healthy amount of paranoia is the best way to ensure your organisation’s guard is never down. If you practice day-to-day prevention – a little training here, a patch or update there – exercising cybersecurity best practices can become a holistic and routine part of your operations, and your business can continue to operate, safe in the knowledge that all bases are covered,’ says Russell.
Kaspersky Lab Africa general manager Riaan Badenhorst agrees. ‘Cybersecurity should be everyone’s priority. We’ve noticed that many companies seem to be spending approximately 80% of their security budgets to try and prevent security breaches, while only 20% is being used to predict, detect and respond to attacks.

‘Local companies, no matter their size, need to change their 80/20 approach to IT security, and become more proactive, as opposed to merely relying on “installing” software to “prevent” an attack.’ Badenhorst warns that technology alone cannot protect a company. ‘Efforts from all departments must be unified and every department must know the company IT security policy,’ he says.
This echoes a recent Kasperksy report, which cautions about what it calls the ‘human factor’ in IT security. The firm warns that careless or uninformed staff are the second most likely cause of a serious security breach (malware being the first). The report notes that ‘in 46% of cybersecurity incidents in the last year, careless/uniformed staff have contributed to the attack’.
The Kasperksy research also cites survey data showing that 57% of businesses now assume their IT security will become compromised and 52% of businesses admit that their employees are their biggest IT security weakness. Meanwhile, a report by CompTIA notes that 60% of cybersecurity risks in South Africa were due to human error – a statistic that mirrors the global total of 58%.
Expert after expert, and report after report, all say the same thing. Cyberattacks and IT security breaches are far more rampant than anyone could imagine. Businesses and organisations of all sizes are woefully ill-equipped to deal with the threat. People are the biggest problem.
The winning strategy for the battle against cybercriminals lies in what McAravey describes as a combination of human and artificial intelligence. ‘The key to utilising an artificial intelligence approach is being able to derive anomalies from the huge amounts of information that are captured in log management solutions and security information and event management systems,’ he says.
McAravey adds: ‘The application of readily available machine learning techniques with anomaly-detection algorithms can help give an organisation “x-ray vision” into activity on their corporate networks and provide an advantage over the attacker.’
However, that artificial intelligence is – as all those experts will tell you – next to useless without human co-operation. ‘Human intelligence is an oft-neglected, yet critical part of the line of defence,’ says McAravey. ‘It’s a game of hearts and minds, and every organisation has to view their employees, contractors and partners as extensions of their firewall.’